#建立cdr
hdiutil create -o /tmp/Mojave.cdr -size 6000m -layout SPUD -fs HFS+J
#掛載cdr至install_build
hdiutil attach /tmp/Mojave.cdr.dmg -noverify -mountpoint /Volumes/install_build
#將Mojave掛載到install_build
sudo /Applications/Install\ macOS\ Mojave.app/Contents/Resources/createinstallmedia --volume /Volumes/install_build
#退出
hdiutil detach /Volumes/Install\ macOS\ Mojave
#轉換成iso
hdiutil convert /tmp/Mojave.cdr.dmg -format UDTO -o ~/10.14.iso
#修改檔名
mv /tmp/Mojave.cdr.dmg ~/10.14.dmg
mv ~/10.14.iso.cdr ~/10.14.iso
分類彙整: os
OS X Terminal Colors
在~/.bash_profile加入
export CLICOLOR=1
export LSCOLORS=Gxfxcxdxbxegedabagacad
export PS1='\[\033[01;32m\]\u@\h\[\033[00m\]:\[\033[01;36m\]\w\[\033[00m\]\$ '
export TERM=xterm-color
將指定資料夾打包成dmg檔案
以Desktop為例
NAME=Desktop
DPATH=~/Desktop
hdiutil create \
-volname $NAME \
-srcfolder $DPATH
-ov \
-format UDZO $NAME.dmg
使用EDNS跟DNSSec保護DNS資料
DNS伺服器扮演著將IP與網域對應的工作.
但因為當初DNS設計並沒有考量安全性的設計,導致至今有許多DNS偽造的情況.
為瞭解決上述問題,衍生出了DNSSec以及EDNS等相關技術的發展.
然而DNS已經行之有年,許多DNS Server並沒有落實EDNS.
所以過去有一段時間,公用的DNS Server對於未支援EDNS的伺服器會採用二次查詢的方式.
也就是第一次會使用EDNS查詢,失敗後改用傳統DNS方式查詢.
如此一來就可以相容兩種系統,但是也造成EDNS遲遲無法普及.
因此幾個公用的DNS Server(如Google 8.8.8.8, GloudFlare 1.1.1.1)約定在2019/2/1這天要來測試只做EDNS查詢,並將這一天稱為DNS Flag Day.
所以當DNS Server不支援EDNS時,將會造成網域名稱無法順利解析.
為避免上述狀況,本研究採用下列方式,開啟EDNS及DNSSec之設定.
下面是有關於如何將DNS提升至EDNS的方法:
1.確定網域名稱,並準備好網域設定檔
DOMAIN=cbe.tw
# 網域設定檔: ${DOMAIN}.txt
2.建立公私鑰
2.1.KSK
KSK_KEY=$(dnssec-keygen -r /dev/urandom -f KSK -a RSASHA512 -b 2048 -n ZONE ${DOMAIN})
2.2.ZSK
ZSK_KEY=$(dnssec-keygen -r /dev/urandom -a RSASHA512 -b 1024 -n ZONE ${DOMAIN})
3.將key附加到網域設定檔 ( 也就是${DOMAIN}.txt )
cat K${DOMAIN}*.key >> ${DOMAIN}.txt
4.產生加簽後的網域設定檔 ( )
dnssec-signzone -o ${DOMAIN} -k ${KSK_KEY}.key ${DOMAIN}.txt ${ZSK_KEY}.key
上述步驟將會產生:
* 加簽過後的網域設定檔,檔名會是 ${DOMAIN}.txt.signed
* DS紀錄檔(DS records),檔名會是 dsset-${DOMAIN}.
![]()
5.啟用DNSSec
* 將${DOMAIN}.txt.signed放到 DNS Server上 (如Bind9 or CoreDNS).
* 到網域註冊商上加入DS records.
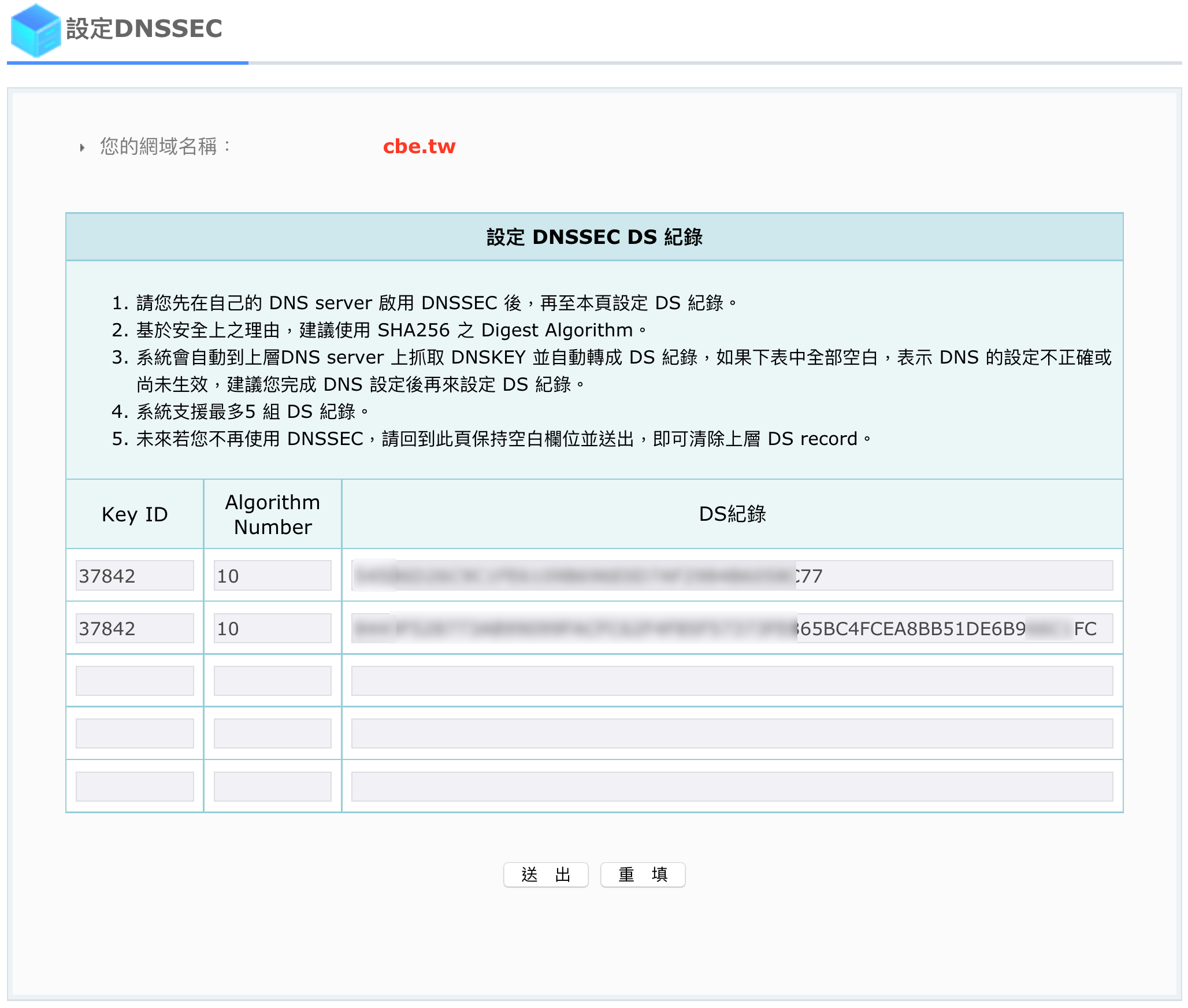
* 開啟TCP 53 port,並做好對應的NAT.
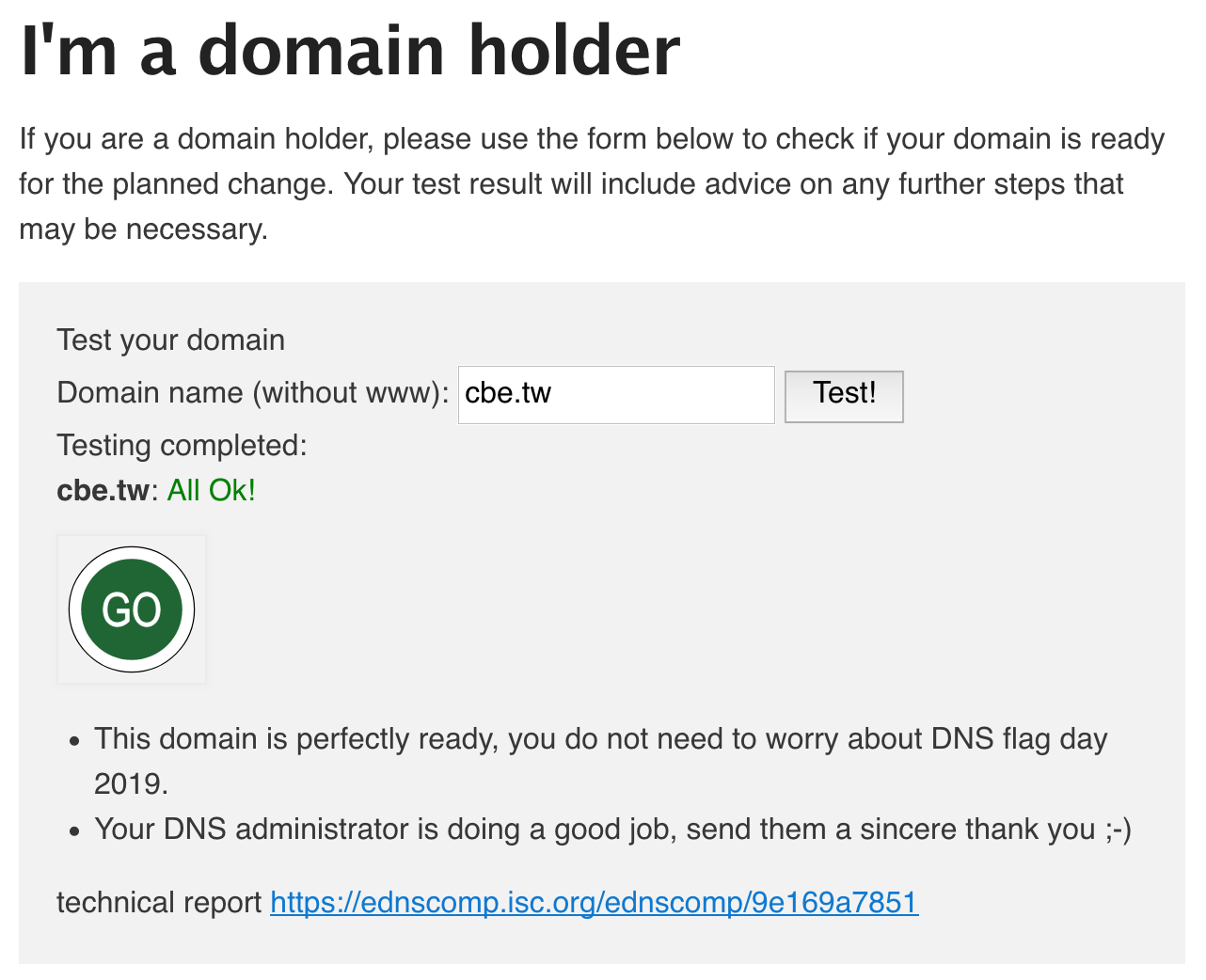
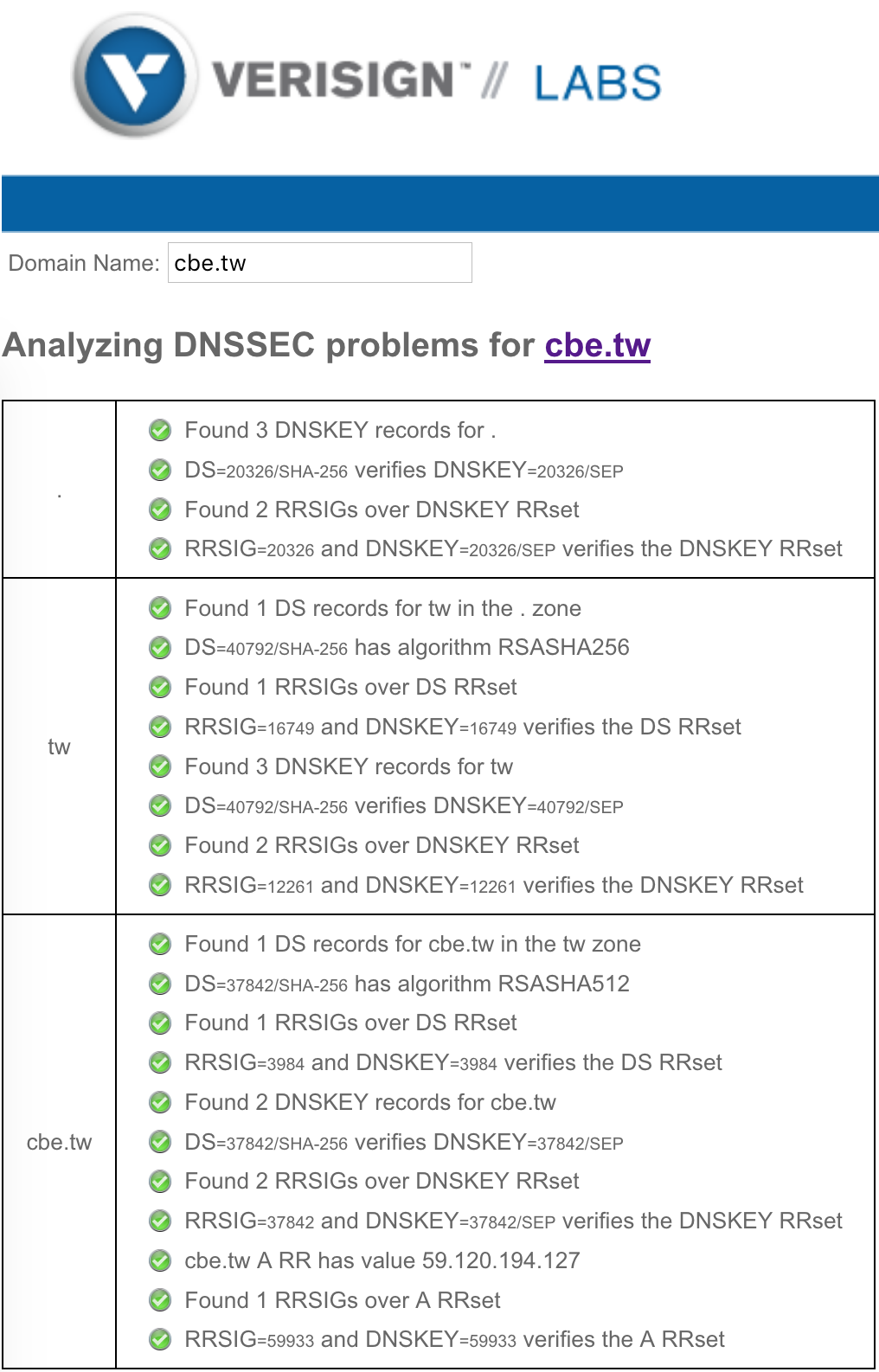
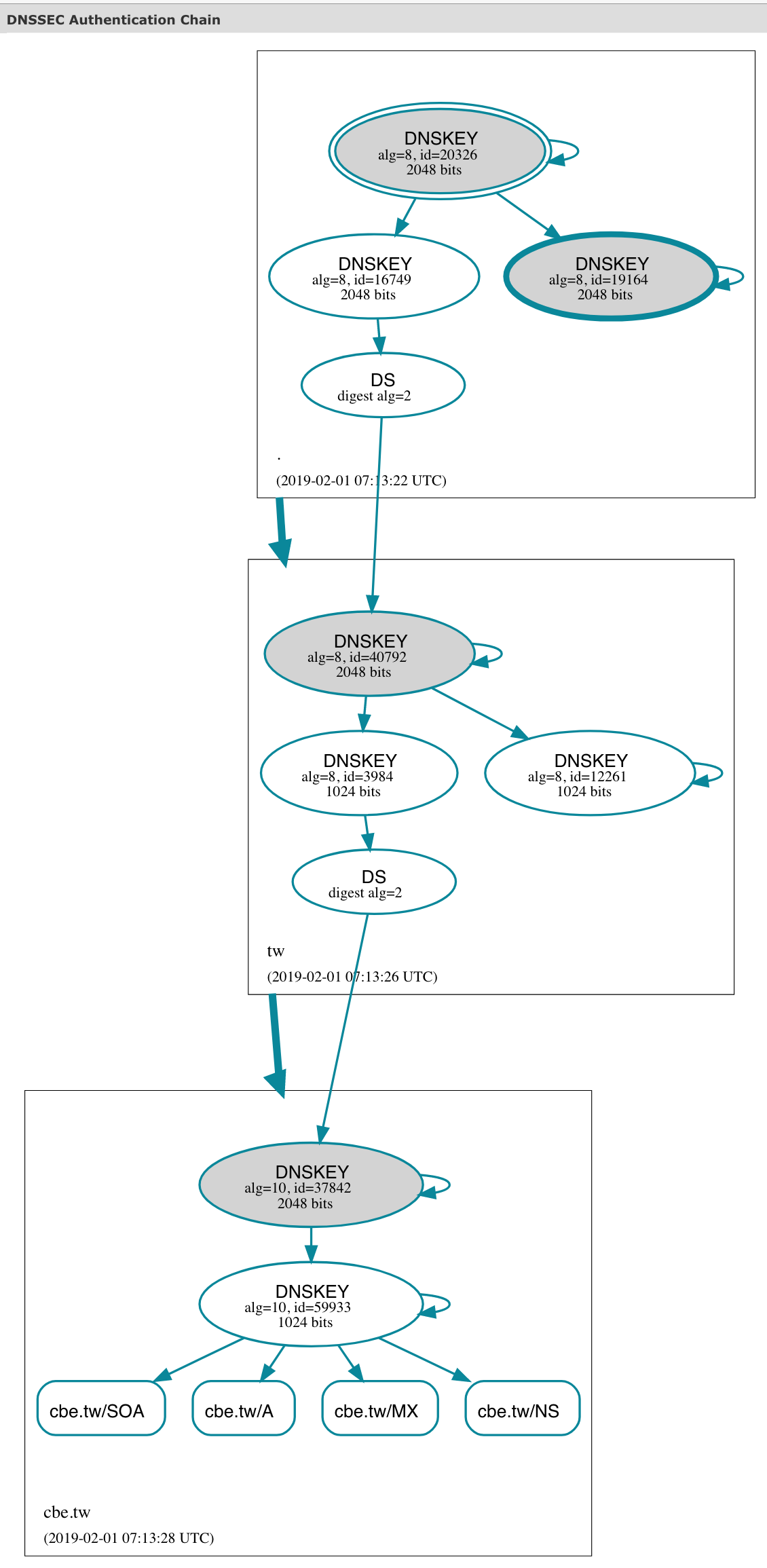
6.檢測
* https://dnsflagday.net/#domain-holders
* https://dnssec-analyzer.verisignlabs.com/
* http://dnsviz.net/
移除XQuartz
launchctl unload /Library/LaunchAgents/org.macosforge.xquartz.startx.plist && \
sudo launchctl unload /Library/LaunchDaemons/org.macosforge.xquartz.privileged_startx.plist && \
sudo rm -rf /opt/X11* /Library/Launch*/org.macosforge.xquartz.* /Applications/Utilities/XQuartz.app /etc/*paths.d/*XQuartz && \
sudo pkgutil --forget org.macosforge.xquartz.pkg && \
rm -rf ~/.serverauth* && rm -rf ~/.Xauthorit* && rm -rf ~/.cache && rm -rf ~/.rnd && \
rm -rf ~/Library/Caches/org.macosforge.xquartz.X11 && rm -rf ~/Library/Logs/X11
refer: https://gist.github.com/pwnsdx/d127873e24cef159d4d603accaf37ee4
經測試,可移除使用dmg安裝的XQuartz
將docker log導向log server
server: 1.2.3.4
port: 514/dup
docker rm -f logspout
docker run \
-d \
--name=logspout \
--restart=always \
-v /var/run/docker.sock:/var/run/docker.sock \
-v /etc/localtime:/etc/localtime \
-p 10080:80 \
-e RAW_FORMAT="{{.Data}}" \
gliderlabs/logspout \
syslog+udp://1.2.3.4:514
docker logs -f logspout
修改docker0網段
其中10.172.254.254是Getway,不要自作主張改成 192.168.1.0/24 or 10.172.0.0之類的..
yum install bridge-utils -y
service docker stop
ip link set dev docker0 down
brctl delbr docker0
iptables -t nat -F POSTROUTING
brctl addbr docker0
ip addr add 10.172.254.254/16 dev docker0
ip link set dev docker0 up
cat << EOF > /etc/docker/daemon.json
{
"bip": "10.172.254.254/16"
}
EOF
systemctl daemon-reload
systemctl restart docker.service
reboot #如果有k8s則需要重開機
在centos 7上安裝nvidia docker
#安裝 docker-ce
yum-config-manager --add-repo https://download.docker.com/linux/centos/docker-ce.repo
yum install docker-ce-18.06.0.ce -y
systemctl enable docker && systemctl start docker
# 移除舊版nvidia-docker
docker volume ls -q -f driver=nvidia-docker | xargs -r -I{} -n1 docker ps -q -a -f volume={} | xargs -r docker rm -f
sudo yum remove nvidia-docker
# 加入repositories
distribution=$(. /etc/os-release;echo $ID$VERSION_ID)
curl -s -L https://nvidia.github.io/nvidia-docker/$distribution/nvidia-docker.repo | sudo tee /etc/yum.repos.d/nvidia-docker.repo
# 安裝 nvidia-docker2
sudo yum install -y nvidia-docker2
sudo pkill -SIGHUP dockerd
# 測試
docker run --runtime=nvidia --rm nvidia/cuda:9.0-base nvidia-smi
centos 7 change desktop icon size
small size
gsettings set org.gnome.nautilus.icon-view default-zoom-level small
list all size
gsettings range org.gnome.nautilus.icon-view default-zoom-level
refer: https://unix.stackexchange.com/questions/250266/rhel-7-gnome-shell-decrease-desktop-icon-size
k8s安裝ingress nginx
ingress-nginx最新版已經不包含default-http-backend.
因此安裝0.20.0
#安裝ingress-nginx
wget https://raw.githubusercontent.com/kubernetes/ingress-nginx/nginx-0.20.0/deploy/mandatory.yaml
sed -i 's/serviceAccountName: nginx-ingress-serviceaccount/hostNetwork: true\n serviceAccountName: nginx-ingress-serviceaccount/g' mandatory.yaml
kubectl apply -f mandatory.yaml
rm -f mandatory.yaml*
kubectl get pod --all-namespaces
#修改ingress-nginx
NODE_COUNT=$(kubectl get nodes | grep -v master | grep -v STATUS | wc -l)
echo $NODE_COUNT
if [ $NODE_COUNT -gt 1 ] ; then
kubectl -n ingress-nginx patch deployment default-http-backend --patch $(echo "{\"spec\":{\"replicas\":$NODE_COUNT}}")
kubectl -n ingress-nginx patch deployment nginx-ingress-controller --patch $(echo "{\"spec\":{\"replicas\":$NODE_COUNT}}")
fi
kubectl get pods -n ingress-nginx -o wide
#更換自製 http-backend image
DOMAIN=ssl.cbe.tw
kubectl -n ingress-nginx patch deployment default-http-backend --patch "{\"spec\":{\"template\":{\"spec\":{\"containers\":[{\"name\":\"default-http-backend\",\"resources\":{\"limits\":{\"cpu\":\"100m\",\"memory\":\"200Mi\"},\"requests\":{\"cpu\":\"100m\",\"memory\":\"200Mi\"}},\"image\":\"slanla/apache-defaultbackend\",\"ports\":[{\"containerPort\":8080,\"protocol\":\"TCP\"}],\"env\":[{\"name\":\"LETSENCRYPT_PROXYPASS_URL\",\"value\":\"http://$DOMAIN/.well-known/acme-challenge/ connectiontimeout=15 timeout=30\"},{\"name\":\"LETSENCRYPT_PROXYPASSREVERSE_URL\",\"value\":\"http://$DOMAIN/.well-known/acme-challenge/\"}],\"livenessProbe\":{\"httpGet\":{\"path\":\"/healthz\",\"port\":8080,\"scheme\":\"HTTP\"},\"initialDelaySeconds\":30,\"timeoutSeconds\":5,\"periodSeconds\":10,\"successThreshold\":1,\"failureThreshold\":3}}]}}}}"
kubectl get pods -n ingress-nginx -o wide
